Why? #
Why should we care about privacy? Most importantly, privacy fosters freedom of thought and speech, which greatly strengthens democracy. It does this by allowing us to hold unpopular opinions without fear of being punished or even killed by those in power, something which has happened many times throughout history and continues today. Being free to express discontent with the current elected officials is necessary to keep their power in check. Because the leaders can be replaced, they are motivated to not abuse their power.
Even when privacy is violated to a lesser extent, the harvested information can cause identity theft, blackmail, or subtle manipulation based on someone’s interests or characteristics. This manipulation can and is even being automated – it’s called “targeted advertisements.” It's often been noted that if you told the current state of privacy to someone 30 years ago, they would be shocked. But it happenes so gradually that we've been accepting the loss bit-by-bit. This level of privacy violation and gradual erosion of people’s expectations of privacy can also be a stepping stone toward an oppressive regime.
When it comes to alone time, privacy is instrumental in being productive, creative, and restful. A nagging feeling that you might be watched, recorded, or tracked in some way can interfere with your activities. Imagine trying to write an essay, but your entire edit history is saved and anyone who reads the essay can see all the dumb half-formed ideas, the unfiltered thoughts, the two-day gap in the edits when you should have been working on it, and maybe the accidental password that was pasted in halfway through. You have all this added pressure of what the process might look like to people, not to mention the normal pressure of what the result will look like. I would be tempted to write the entire essay in a separate document and paste it in when I was done! That urge is a desire for privacy, not because I am ashamed of my process, but because I already have enough to think about when writing, and adding more to consider would really slow me down. The observation would alter the result.
You might say, “If I have nothing to hide, then why should I care about privacy?” Well, the best way to convey my reasoning about that sentiment is to paraphrase a quote from Glenn Greenwald’s TED Talk. If you truly have nothing to hide, give me access to all your email accounts, not just your respectable work email, and I will read through all your emails and publish whatever I find interesting. “After all, if you're not a bad person, if you're doing nothing wrong, you should have nothing to hide.” Glenn says that no one has ever taken him up on this offer. It’s interesting that this ideal we have in our heads that an invasion of privacy only affects bad people turns out quite differently when put to the test. None of us want Glenn poking around in our emails, much less someone who doesn’t bother to ask nicely for access. We all want to keep our emails and other information private – maybe it could be misrepresented if published, maybe it was a highly personal moment, maybe we don’t want people to know where we live, or maybe we just don’t want everyone (or an algorithm) to know how slowly we respond to emails sometimes. Privacy gives us room to breathe.
Criteria #
Now that we have discussed why privacy is important, what makes something private, at least in the digital sense? One thing you might have encountered is an app that requires a ton of permissions to install (Figure 1). Many apps don’t need these permissions to operate, and are only asking for them so they can collect your information and sell it to an advertisement company. A request for way too many permissions is a telltale sign that the app probably does not respect your privacy. You can also do some research on the app to see what professionals have found and make a more informed decision whether to install it or not.
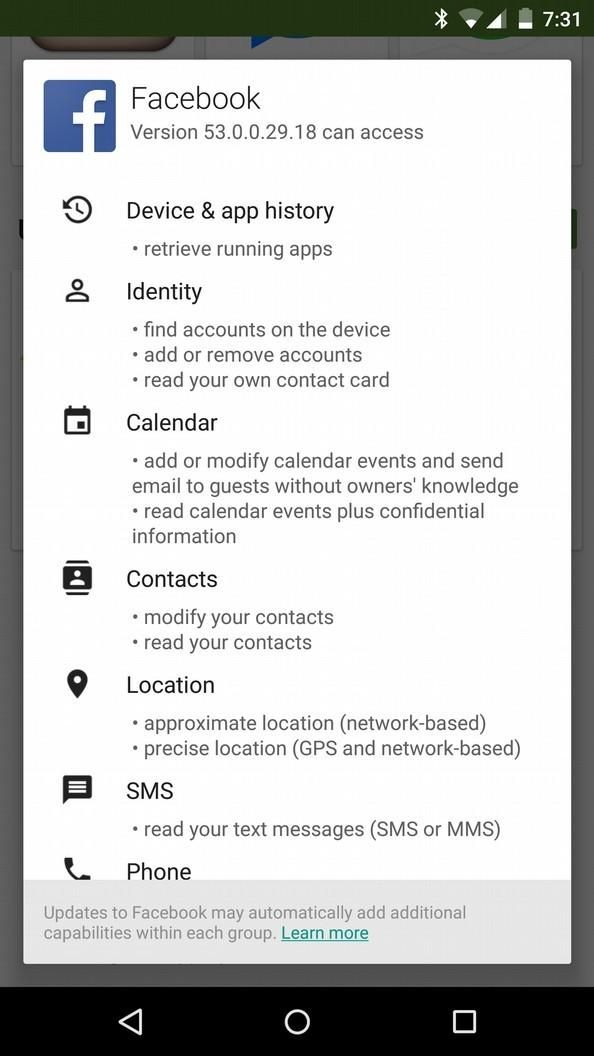
Figure 1: The Facebook Android app requires a ton of permissions
Speaking of advertisement companies, another litmus test is the saying, “If it’s free, you are the product.” (In this case, free refers to gratis, free as in “free of charge”, as opposed to libre, free as in “Give me liberty, or give me death!”) Find out how an app makes money, and if it uses targeted ads, it usually sells your data to a targeting company such as Google or Facebook, which builds a profile of you as accurately as possible in order to send you ads for things they think you will want. Facebook even estimates your big 5 personality type to compare you with similar people. This collection of your information can even happen within your operating system, such as in Microsoft Windows, which sends information back to Microsoft anytime your computer is running.
So far, we have only discussed software that doesn’t respect your privacy, so here are some characteristics of software that does. In addition to not requesting excess permissions and not sending personal data back, most privacy respecting software is free (as in libre) and open source (FOSS). This refers to software that publishes the source code, which is like the recipe for making the software. If an app is FOSS, you can see what experts have said about its privacy, and they can check the source code to verify that it does not steal your data. Remember for later in this guide: FOSS means the recipe is available.
Another common aspect of good privacy-respecting software is end-to-end encryption (E2EE). Imagine sending texts, but you have a secret code with your friend. You can send them a message in that secret code, and you know that no one else can read it, not even the app you sent it through. E2EE is that, but with a lot more math – I’ll spare you the cryptographic details. It’s called end-to-end because only you and your friend, the two ends of the communication, can understand the message. This is different from other forms of encryption, which can be confusing, so make sure to look for E2EE specifically on any chat apps you use. Some examples are Element.io and Signal. Some apps claim to have E2EE, but have some controversy, such as WhatsApp. The details are more complicated, involving metadata, which is info about who is texting who, and backdoors, which are intentional gaps in security meant for the good guys, but which always get exploited by the bad guys.
I will briefly outline a few other concepts that aid privacy here, but keep in mind that there is much more information on these topics available online. It’s just a quick Google search away, or should I say DuckDuckGo search (Figure 2). Being anonymous means that your activity cannot be linked back to you. Being pseudonymous means mostly the same, but people can tell it was the same unknown person doing the activity each time. An app has amnesia if it forgets about all your activity each time it starts up, which helps with some aspects of anonymity. An app is decentralized if there is no single company, person, government, or other entity controlling it. Rather, each user has a little bit of control and together they steer the platform.

Figure 2: [DuckDuckGo](https://duckduckgo.com/), the search engine that doesn't track you.
DuckDuckGo is the most popular alternative to Google search and so it's probably the best for beginners. However, it isn't FOSS, so if you are looking for a FOSS search engine, look into Searx.me.
Easy Steps to Take #
So, what can be done to achieve complete online privacy? Well, unfortunately there is no one-size-fits-all snake oil solution, but we’ll start with some simple steps that you can do in just a few minutes, then move to some more comprehensive plans. The most effective step for its simplicity is installing the Tor Browser (Figure 3) on your phone or laptop. To the user, the Tor Browser works just like a normal web browser (such as Chrome or Firefox), where you can search things, click on links, etc. But behind the scenes, it has a lot of good properties we discussed before (it is FOSS, is encrypted, is anonymous, has amnesia, is decentralized, and even uses DuckDuckGo). The biggest downside is that the Tor Browser is slower than a normal browser, but even if you only use it some of the time, it’s a huge improvement over just using a normal browser. Having it installed lets you find information without having to worry about your searches being sold to keep building that detailed profile of your activity. Go ahead and give it a try by installing it on your phone, laptop, or tablet: https://www.torproject.org/download/. There are some things to keep in mind when using the Tor Browser. First, if you do anything to identify yourself, such as log in to your email or another account, none of the browser’s protections can keep you anonymous, since you just identified yourself to the website you logged into. Second, this only one step to protect your privacy, as anything you do outside the browser (such as running the Google Maps app on your phone) will of course still be linked to you.

Figure 3: [The Tor Browser](https://www.torproject.org/) - Defend yourself against tracking and surveillance. Circumvent censorship.
Another step you can take to increase your privacy is to sign up for and invite your friends and family to sign up for an E2EE chat app or email such as Matrix/Element.io, Signal (Figure 4), Tutanota Mail, or Protonmail. All of these are available for your phone and laptop. Now you can send messages to each other that only you can read, a policy enforced by the power of mathematics! And the interfaces are simple enough that you don’t need to worry how it works.

Figure 4: [Signal](https://signal.org/) - End-to-end encrypted texting
If the Tor Browser doesn’t appeal to you or is too slow, there are some minor changes you can make to your normal browser’s settings to get some privacy, although this will not hide your IP address (which tells your approximate location). The simplest change is to set DuckDuckGo.com as your browser’s search engine instead of Google by going to duck.com and clicking on “Add DuckDuckGo to <Firefox/Chrome/Other>.” There are also some browser extensions that will reduce the amount of information that your browser leaks. For Chrome, go to https://chrome.google.com/webstore/ and for Firefox, go to https://addons.mozilla.org/. To give your browser amnesia, so that it erases some of its memory every time you open it, search for Cookie AutoDelete and install it. Keep in mind that this will not erase a website’s memory of you completely, because there are other ways of identifying you, but it is a good start. To block ad tracking, use uBlockOrigin (for Chrome) or Adnauseam (for Firefox). To block another kind of tracker that uses font libraries, among other things, use Decentraleyes.
One last easy step if you have an Android phone is to install F-Droid from https://f-droid.org/ which is an entire app store of FOSS apps that you can browse. To install it, go to the site and click on “Download F-Droid,” and you will have to enable installing from unknown sources in your phone’s settings. A useful FOSS app in the store is NewPipe, which is a YouTube app without as much tracking and some extra features, but there are many other great apps.
Further Steps to Take #
After getting your feet wet with solutions that you can add to your existing setup, let’s take a gander at some solutions that involve subtracting or substituting apps, which will be a little more disruptive, but still doable. Starting off with one of the simpler substitutions is trading out Microsoft Office for LibreOffice (Figure 5). LibreOffice office suite that has all the features that most general users expect from Microsoft Office, at a fraction of the price. And that fraction is zero! LibreOffice is completely free of charge as well as being FOSS, and it can also run on Windows, Mac, and Linux. My family has been using LibreOffice and its predecessor, OpenOffice, for as long as I can remember, and we have saved a lot of money from just not buying Microsoft Office. As an added bonus, there are absolutely no tracking or privacy concerns involved with LibreOffice.

Figure 5: [LibreOffice](https://www.libreoffice.org/) - a free and powerful office suite
Facebook has had so many data breaches over the years, not to mention the tracking of its own users even on the off-days when no hackers are in. If you have a Facebook account, consider reducing your usage until you are at a point where you don’t need it anymore, and can safely delete it. If deleting it is not an option, at least uninstall the phone app, which includes a lot of extra tracking, and install Frost from the F-Droid store, which will allow you to log in and use Facebook without giving it permission to access your contacts, calendar, etc. Better yet, limit your access to only be through the Tor Browser (still works on your phone or laptop), by logging in on Facebook’s dedicated tor website at https://www.facebookcorewwwi.onion/ which you can only get to from the Tor Browser. They still know it’s you because you are logging in with your username, but they don’t know what location you are logging in from. Unless, of course, you post a picture that contains a geotag.
If you reduce usage of Facebook or hopefully delete it altogether, what options are available to replace it? Well, there is a set of FOSS social media sites that are starting to gain users as a replacement for Twitter, Facebook, Instagram, YouTube, etc. They are called Mastodon (Figure 6), Diaspora, PixelFed, PeerTube, and others. I say “set of sites” because these different sites actually talk to each other. Imagine if you could tweet at a Facebook user, view an Instagram page from Twitter, subscribe to a YouTube channel from Instagram, or even friend a Facebook account from MySpace! The point is that these new social media sites are “federated” which is a form of decentralization similar to email. You have different email providers (Gmail, Yahoo, Hotmail, Protonmail), but you can still send emails to and from any of these, which makes email a federated system. What’s more, each one has multiple instances of the site run independently by different people. I recommend signing up for https://mastodon.social/ as a start, since it is the most popular, but you can always migrate your account to another site later if you want.

Figure 6: [Mastodon](https://joinmastodon.org/) - Social networking, back in your hands
Another possible transition is to sign up for a Nextcloud (Figure 7) account. Nextcloud is basically a complete FOSS replacement of Google Drive and then some, including video calls, file storage, calendar, contacts, online editing, todo lists, notes, forms, music, and countless other apps that are all integrated together into one site. Signing up is relatively easy, and it has apps for iOS, Android, Linux, Windows, MacOS, that can sync all your files, calendar, contacts, etc. to every device you own if you want to. I personally run a Nextcloud server for my whole family and many of my friends, so you can contact me if you want an account, or you can sign up for one of the many other providers that have a more streamlined process directly through the app, which generally have 5GB of space free. If you want more space, you generally have to pay a small monthly fee depending on the provider.

Figure 7: [Nextcloud](https://nextcloud.com/) - The self-hosted productivity platform that keeps you in control
Have you been hearing about the YouTube demonitization recently? Basically, content creators on YouTube are having ad revenue pulled from their videos if they mention certain topics that are not deemed “advertiser friendly.” Of course, you could argue that creators are not entitled to earn money just because they post a video. Or, instead of arguing, you could just tell your favorite creators to sync their videos to LBRY (Figure 8), a new site where many YouTubers are already earning money from an alternative cryptocurrency-based (like Bitcoin, but different) system of shared, decentralized storage. Also, in December of 2019, several channels that were talking about cryptocurrency were suddenly deleted by YouTube, despite not breaking any of the community guidelines. Where do you think those nerds went? Right over to LBRY. There are other alternatives to YouTube, such as PeerTube, which is also decentralized, but doesn’t have as many creators as LBRY. If you still want to watch YouTube videos, but want to reduce the amount of tracking, go to https://yewtu.be/ which gives you access to all the YouTube videos through a different, more private, interface. You can even subscribe to YouTubers without making an account.

Figure 8: [LBRY](https://odysee.com/) - a secure, open, and community-run digital marketplace.
Steps that Require More Effort #
Now that we have covered some of the more basic replacements, we will take a look at some more things to replace that will require a little more effort, but will make a good impact. First, it’s good to take stock of what accounts you have online. Maybe you have a physical password book that has all your accounts listed. To organize these and also keep track of passwords in a more secure way, you can use a password manager such as KeePassXC, LastPass, DashLane, or BitWarden. I use KeePassXC because it just stores the passwords as a file, with no fancy cloud storage with the increased possibility of being hacked. Make sure to back up the file in multiple places, otherwise you could lose access to your accounts. Once you have picked a password manager, copy the accounts from your password book. If you don’t have a password book, try to remember as many accounts as you can. There’s not much advice I can give on this step as it depends on how you have been storing passwords until now. But having a password manager makes the next step, transitioning emails, a lot easier.
We should address the elephant in the room, email. If you have a Tutanota (Figure 9) or Protonmail (Figure 10) account, and are looking to transition your old Gmail, Yahoo, or other account, here is how I did it. First, I signed up for both a Tutanota and Protonmail account to see which one I liked better. Then after choosing Tutanota for reasons irrelevant here (both are great and will work for these instructions), I set up forwarding from my old Gmail account to my new Tutanota account. Then I went through my KeePassXC to see what all accounts were associated with my Gmail. I manually logged in to each one and either deleted the account (if I didn’t need it anymore), or set the email address to my Tutanota. Then, every few weeks, I looked at what emails were still forwarded from Gmail, and changed those over to Tutanota as well. At a certain point I sent one bulk email to all my friends and family (from my Gmail so they knew it was me) telling them about my new email address. This whole process didn’t take as long as I thought, especially since I could just wait a few weeks to see if any emails slipped through the cracks to the old address. Now, the effect of all this is that Google no longer has access to all my emails in one place, although they do have a big chunk of my emails since most people send to me using Gmail. The partial solution for this was to get my family Tutanota accounts for Christmas a few years back, which turned out to be a success. Although my family hasn’t fully transitioned to Tutanota like I described here, they routinely use it for sending tax and health forms, and other boring but importantly private information.

Figure 9: [Tutanota](https://tutanota.com/) - the world's most secure email service, easy to use and private by design.

Figure 10: [ProtonMail](https://proton.me/) - Secure Your Communications
To upgrade your phone to a more private alternative, you have two options. The first one is to pre-order a PinePhone for $150, which is built from the ground up to be privacy-respecting. The other option is to install LineageOS on an Android phone. LineageOS is a FOSS operating system that is basically Android minus Google. You can do calls, texts, etc. and you can use the F-Droid store for a more limited set of apps than normal Android. The huge benefit is that you have removed Google from your pocket without spending any money and can still make phone calls, which is quite an achievement in the modern day. Make sure to back up everything on your phone before installing LineageOS.
Now it’s time for the biggest change of them all – switching to Linux (Figure 11)! Don’t be scared, for starters my Mom actually uses Linux right now despite having no technical knowledge. Contrary to some misconceptions, Linux is not a text interface with the matrix letters scrolling past. Rather, it is a FOSS operating system with a point and click user interface like Windows or MacOS. Switching to Linux eliminates any private data collection by the operating system since it is FOSS and the Linux community keeps things accountable. There are many Linux’es to choose from, but to keep things simple, we will use Ubuntu. The easiest way to try it out is by setting up an Ubuntu virtual machine with VirtualBox, which you can do by DuckDuckGo’ing “setting up an Ubuntu virtual machine with VirtualBox” (beyond the scope of this guide, but shouldn’t take too long). After using Ubuntu in a virtual machine (VM), you might eventually want to install it on a real computer. Again, back up everything before you install. The install process is documented in many places online; all you need is a USB drive and a willing laptop, and you can finally trade that virtual machine for a reality.

Figure 11: Linux - FOSS Operating System
Conclusion #
This has been a guide to taking back your online privacy, using some of the many tools that are available online. To continue the journey, you can find more information about privacy at https://www.privacytools.io (Encryption and tools to protect against global mass surveillance), and you can find more software alternatives at https://switching.software (Ethical, easy-to-use and privacy-conscious alternatives to well-known software). If you have any comments, questions, or suggestions, contact me securely
Other Great Articles #
The Harm That Data Do by Scientific American - Paying attention to how algorithmic systems impact marginalized people worldwide is key to a just and equitable future Why Your Individual Privacy Matters for the Wider Population by The New Oil
My Links #
Here are some links to my profile on some private services I use, some of which I mentioned in this guide:
- contact me securely with Tutanota, Protonmail, or Element.io
- my Mastodon profile, which is on an instance called FOSStodon, named after FOSS (Free and Open Source Software, as mentioned in the guide)
- my videos on PeerTube, on the diode.zone instance
- my videos on LBRY
- my LBRY referral link, which you should use when signing up to give both of us a bonus
- my YouTube videos through invidious as an example